| Previous | Table of Contents | Next |

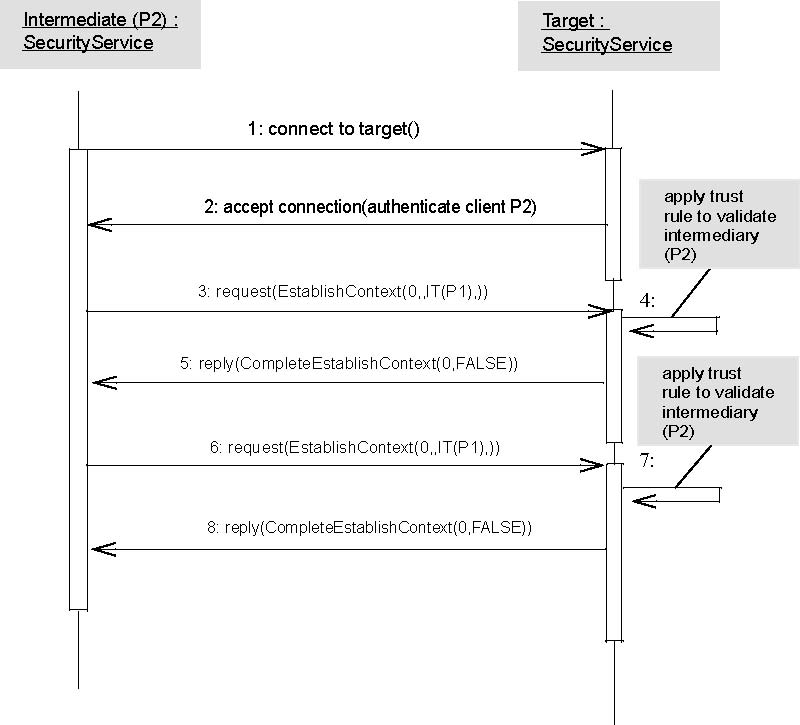
1. Initiate SSL/TLS connection to TSS.
2. SSL/TLS connection and ciphersuite negotiation accepted by both CSS and TSS. CSS evaluates its trust in target authentication identity and decides to continue. Client (P2) authenticates to TSS in the handshake.
3. Send request (with stateless security service context element containing spoken for identity (P1) in identity_token).
4. TSS validates that target trusts P2 to speak for P1.
5. Receive reply with CompleteEstablishContext service context element indicating context (and request) was accepted.
6. Same as 3.
7. Same as 4.
8. Same as 5.
24.7.3.1 Sample IOR Configuration
The following sample IOR was designed to address the related scenario.
CompoundSecMechList {stateful = FALSE;mechanism_list = {
CompoundSecMec { target_requires = {Integrity, Confidentiality, EstablishTrustInClient}; transport_mech = TAG_TLS_SEC_TRANS
{
target_supports = {Integrity, Confidentiality, EstablishTrustInClient,
EstablishTrustInTarget}; target_requires = {Integrity, Confidentiality, EstablishTrustInClient}; addresses = {
TransportAddress { host_name = x; port = y;
};
};};as_context_mech = {
target_supports = {};
... }; sas_context_mech = {
target_supports = {IdentityAssertion};target_requires = {};privilege_authorities = {};supported_naming_mechanisms = {GSSUPMechOID};supported_identity_types = {ITTPrincipalName};
};};};};
24.7.3.2 Validating the Trusted Server
If trust is not presumed, then the TSS shall evaluate the trustworthiness of the speaking for identity (i.e., the client identity
established in the authentication layer(s) - P2 in the preceding example) in order to determine if it is authorized to speak
for the spoken for identity (i.e., the non-anonymous identity represented as P1 in the identity token in the preceding example).
24.7.3.3 Presuming the Security of the Connection
There are variants of this scenario where either no security is established in the connection, or the connection is used to
establish confidentiality only, and/or trust in the target only. These cases all fall under what is referred to as a presumed
trust association. Where the security of the connection and the party using it is presumed, the TSS will not validate the
trustworthiness of the speaking-for identity.
CompoundSecMechList {stateful = FALSE;mechanism_list = {
CompoundSecMec {target_requires = {Integrity, Confidentiality};transport_mech = TAG_TLS_SEC_TRANS {
target_supports = {Integrity, Confidentiality, EstablishTrustInTarget};target_requires = {Integrity, Confidentiality};addresses = {
TransportAddress {host_name = x;port = y;
};
};};as_context_mech = {
target_supports = {};
...};sas_context_mech = {
target_supports = {IdentityAssertion};target_requires = {};privilege_authorities = {};supported_naming_mechanisms = {GSSUPMechOID};supported_identity_types = {ITTPrincipalName};
};};};};